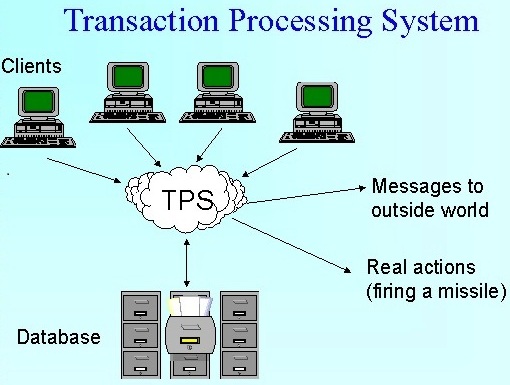
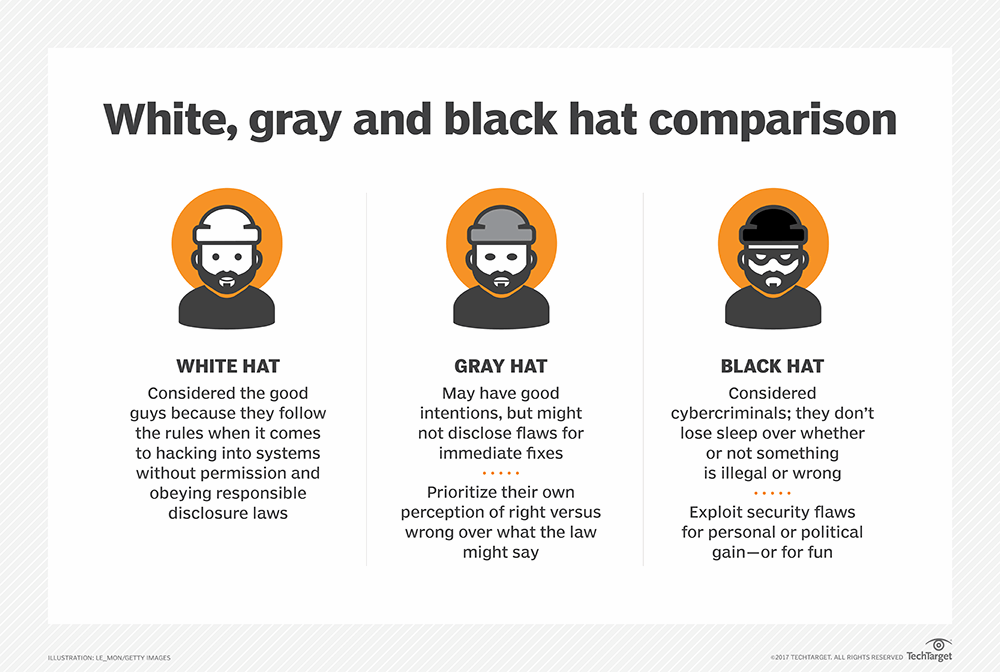
Choose FOUR (4) protocols and discuss its details and importance in network. Research how the aid network Security.
What is Network Protocols
- A network protocols means a formal standards and policies that consists of rules, procedures and formats that determine communications between two or more devices over a network. It govern (control) end-to-end processes of data or network communication in a timely, secure and manageable manner.
- Examples of Network Protocols such as HTTP, HTTPs, FTP, SMTP, DNS and etc.
What is Domain Name Systems (DNS)?
- Domain Name System (DNS) is a hierarchical naming systems built on a distributed database. The system changes the domain name to an IP address and makes it easier to assign domain name to a group of Internet resources and users, regardless of the entities physical location.
- For example of DNS is when a user type google.com into a web browser, the server behind the scenes will map the name to the corresponding IP address like example 121.12.12.123.
What is Secure Sockets Layer (SSL)?
- A Secure Sockets Layer (SSL) is developed by Netscape and defined as a standard protocol used for the secure transmission of documents over a network. The SSL technology creates a secure link between a Web server and browser to ensure the security transmission of private and integral data. It uses Transport Control Protocol (TCP) for communication.
What is File Transfer Protocol (FTP)?
- A File Transfer Protocol (FTP) also known as RFC 959. It is a client/server protocol that used for transferring or exchanging files with a host computer. It can verified with a username and password. Other than that, it allows users to access files, programs and other data from internet sources without using a user ID or password. Some of the web sites use anonymous or guest as a user ID and an email address as a password. FTP is also the internet standard for moving or transferring files from one computer to another using TCP/IP networks.
What is Simple Mail Transfer Protocol (SMTP)?
- A Simple Mail Transfer Protocol (SMTP) also knows as RFC 821 and RFC 2821. It is defined as a standard protocol for email services on a TCP/IP network where it provides the ability to send and receive email messages. SMTP also an application layer protocol that allows for the transmission and delivery of email over the internet. It was created and maintained by the Internet Engineering Task Force (IETF).
References:
- What are Network Protocols? - Definition from Techopedia. (2019). Techopedia.com. Retrieved 23 October 2019, from https://www.techopedia.com/definition/12938/network-protocols
- What is the Domain Name System (DNS)? - Definition from Techopedia. (2019). Techopedia.com. Retrieved 23 October 2019, from https://www.techopedia.com/definition/24201/domain-name-system-dns
- What is the Secure Sockets Layer (SSL)? - Definition from Techopedia. (2019). Techopedia.com. Retrieved 23 October 2019, from https://www.techopedia.com/definition/24025/secure-sockets-layer-ssl
- What is File Transfer Protocol (FTP)? - Definition from Techopedia. (2019). Techopedia.com. Retrieved 31 October 2019, from https://www.techopedia.com/definition/1872/file-transfer-protocol-ftp
- What is Simple Mail Transfer Protocol (SMTP)? - Definition from Techopedia. (2019). Techopedia.com. Retrieved 31 October 2019, from https://www.techopedia.com/definition/1710/simple-mail-transfer-protocol-smtp