Exercise: Systems and Technologies
Explain each system and include the features, advantages and disadvantages. Identify in which level does it operate. Provide diagram where necessary.
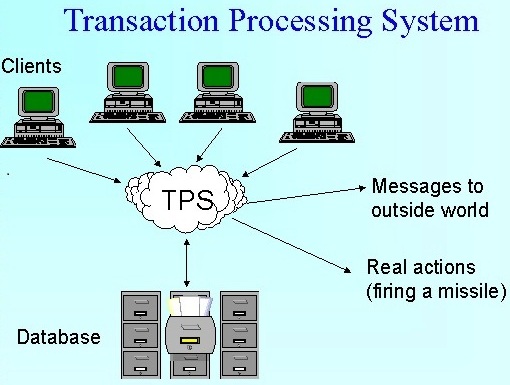
1. Transaction Processing Systems (TPS)
- It is s type of Information System that use in everyday operation which functions as a collecting, storing, modifying and retrieving the data transactions of an enterprise.
- Features:
- Must be two parties
- It takes two parties for the transaction to take place. There cannot be a giver unless there is a receiver. e.g. X borrows $10,000 from a bank. So it can defines as a transaction happens since there a two parties (X and Bank).
- Must be measurable in terms of money
- The event is not consider as a transaction if it is not financially viable
- Advantages:
- Operations handling
- able to handle several transaction at once and making your online transaction process easier as the system provide online processing process.
- e.g. thousand purchases, debit accounts, hold each person's private banking and address information, process customer orders
- Untapped Market
- able to reach and gain customers from around the world which allow people to access and buy your business's products or services.
- Disadvantages:
- High setup costs
- Lack of standard formats
- Hardware and software incompatibility
- The Operational decision are the level of business decision operating at TPS.
- e.g. receipt / banking process / employee data / inventory / sales orders / purchasing transactions / sales transactions.

2. Management Information Systems (MIS)
- An MIS provides managers with information and support for effective decision making, and provides feedback on daily operations.
- Providing information from TPS.
- Features:
- Flexible - allows analysation and evaluation of data from multiple sources and in multiple ways or processing. It allows the introduction of new ways to process data.
- Easy to use - managers does not need advanced knowledge in information systems in order to get the information they need.
- Reliable and accurate - to improve efficiency in the organisation and ensure the decision making is of high quality.
- Advantages:
- Better decision making - by providing relevant information to decision makers.
- It is an integrated systems which allows communication among executives, managers, department heads and employees to improve
- Better communication = better management
- Quality of products or services improves by referring to information about customer feedback and past experiences.
- Disadvantages:
- Expensive to setup and maintain - you need to buy the systems to apply MIS
- Need to learn technical skills to use MIS
- Need to keep up when new tools are integrated into the system
- Upgrading the system requires extra money and staff
- Possibilities of data breach as MIC is connected online
- The Tactical decision are the level of business decision operating at MIS.
- e.g. Scheduled report / Demand report / Key-indicator report / Exception report.

3. Decision Support Systems (DDS)
- It is use to supports business or organizational decision-making activities. DSS serve the management, operations and planning levels of an organizations (usually mid and higher management) and help to make decision, DSS can be either fully computerized, human or a combination of both.
- Features:
- Facilitation - DSS facilitate and support specific decision making activities and decision process
- Interaction - it is a computer-based systems design for interactive use by decision makers or staff
- Advantages:
- Time saving
- Enhance effectiveness
- Improve interpersonal communication
- Competitive advantages
- Cost reduction
- Increase decision maker satisfaction
- To promote learning
- Improves personal efficiency
- Disadvantages:
- Monetary cost
- Overemphasize decision making
- Assumption of relevance
- Unanticipated effects
- Obscuring responsibility
- False belief in objectively
- Status reduction
- Information overload
- The Strategic decision are the level of business decision operating at DDS.
- e.g. Product pricing / profitability / forecasting / risk analysis system.

4. Expert Systems (ES)
- User supplies facts or other information to the expert system and receives expert advice or expertise in response.
- An intelligent computer program that uses knowledge and inference procedures to solve problems that are difficult enough to require significant human expertise for their solution.
- Features:
- Advantages:
- Low accessibility cost
- Fast response
- Not affected by emotions unlike humans
- Low error rate
- Capable of explaining how they reached a solution.
- Disadvantages:
- ES have no emotions
- Common sense is the main issues of the ES
- It is developed for a specific domain
- It needs to be updated manually. It does not learn itself.
- Not capable to explain the logic behind the decision.
- There is NO LEVEL for ES because all the decision is decide by the systems not by the operation / a person.
- e.g. Diagnose of human illnesses / make financial forecasts / schedule routes for delivery vehicles.
References:
- what is transaction processing system - Google Search. (2019). Google.com. Retrieved 4 November 2019, from https://www.google.com/search?q=what+is+transaction+processing+system&safe=active&sxsrf=ACYBGNSE4GF-EBjnZSjbHS0mGwDJw6W8Hw:1572849278621&source=lnms&tbm=isch&sa=X&ved=0ahUKEwjEgKaU-M_lAhW1yosBHYEkCqwQ_AUIEigB&biw=704&bih=768#imgrc=r10XQ_OIhcvPXM:
- Feature of Transaction - AccountingExplanation.com. (2019). Accountingexplanation.com. Retrieved 7 November 2019, from http://www.accountingexplanation.com/features_of_transaction.htm
- Benefits of a Transaction Processing System in Business. (2018). Techfunnel. Retrieved 7 November 2019, from https://www.techfunnel.com/fintech/benefits-of-a-transaction-processing-system-in-business/
- what is management information system - Google Search. (2019). Google.com. Retrieved 4 November 2019, from https://www.google.com/search?q=what+is+management+information+system&safe=active&sxsrf=ACYBGNR86DL89Zfa8sMP0P6BMWYEQ6kY3w:1572850380232&source=lnms&tbm=isch&sa=X&ved=0ahUKEwiMhMuh_M_lAhXYwosBHW8cAZcQ_AUIEigB&biw=704&bih=768#imgrc=ytjP9Z71kGkKsM:
- What is transaction processing system - Google Search. (2019). Google.com. Retrieved 4 November 2019, from https://www.google.com/search?safe=active&biw=704&bih=768&tbm=isch&sxsrf=ACYBGNR_tl4FG2Oe5VMbYHVQjdfEW1342g%3A1572850702799&sa=1&ei=Dsy_Xf2sMNf6wQOfyJzYBQ&q=what+is+transaction+processing+system&oq=what+is+transa+system&gs_l=img.3.0.0i7i30.323401.325875..327803...0.0..0.208.1008.0j5j1......0....1..gws-wiz-img.......0i8i7i30.6I_lJKOZNNs#imgdii=9TzXm8ed-GocUM:&imgrc=r10XQ_OIhcvPXM:
- what is decision support system - Google Search. (2019). Google.com. Retrieved 4 November 2019, from https://www.google.com/search?safe=active&biw=704&bih=768&tbm=isch&sxsrf=ACYBGNRkxjfc72ByFfQSTDKdGUzZ3oOUOQ%3A1572851032551&sa=1&ei=WM2_XZWWIeLxhwP-upyICA&q=what+is+decision+support+system&oq=what+is+decision+susystem&gs_l=img.3.0.0i7i30j0i8i7i30l2.122936.126935..129342...1.0..0.217.1968.0j13j1......0....1..gws-wiz-img.......0j0i8i30j0i24.tGZJ5AkyUWk#imgrc=9ujfxQZPj9ShtM:
- Expert Systems - GeeksforGeeks. (2018). GeeksforGeeks. Retrieved 4 November 2019, from https://www.geeksforgeeks.org/expert-systems/